Just before IIS 8. 0, server administrators may permit or deny accessibility for particular IP address or range of IP addresses. Other then still acquiring IP address that trigger mass attack was tedious process for server administrator because it involve analyzing IIS 8 log periodically and manually add it to deny record whether it found new IP address.
An answer to above issue is instead of blocking IP based mostly on addresses, we must block IP primarily based on it is activity. For example, maximum no of concurrent request, total no of request in excess of a time period, and many others. Sure this really is wherever IIS 8. 0 and Dynamic IP Addresses & Domains Restrictions are available in picture. Dynamic IP Addresses & Domains Restrictions attribute of IIS 8. 0 allow administrators to block IP based mostly on it is activity.

Blocking access based mostly on no of requests in IIS 8
First, Open up IIS manager and navigate to web page for that you desire to configure and click on IP Address and Domain Restrictions function.
Next step, click Edit Dynamic Restriction Settings... link in action pane as shown on the picture below.
Select on it will open up the dialog box that permits you to configure dynamic IP blocking. There will be 2 choices to block IP based mostly on his activity.
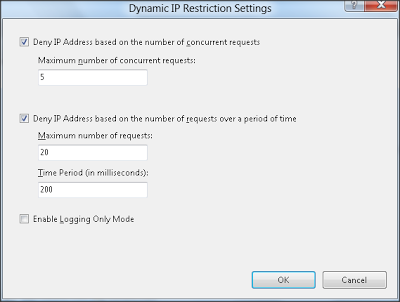
Maximum no of concurrent requests
This setting ensures that in case concurrent requests of any IP address exceed than configured limit then IIS won't serve which ask for and it'll deny.
Maximum no of requests more than a period of time
This setting ensures that in case any IP address sends additional requests than authorized limit among specified time then IIS won't serve which ask for and it'll deny. For e. g. as shown in above image in the event any IP can deliver greater than 20 requests among 200 milliseconds then IIS can deny to serve request.
Response behavior when denying requests
To configure response behavior when denying any requests in IIS 8, click on Edit Feature Settings... link in action pane on right side bar.
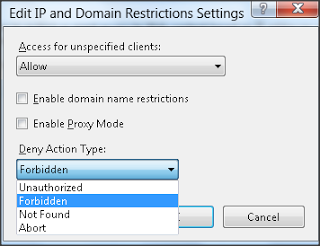
In beneath image we will notice available deny action type while denying any requests. These are generally Unauthorized, Forbidden, Not Found, and Abort. Based mostly for this settings IIS can deliver response along with respective HTTP status code.
Dynamic IP restrictions and Proxy
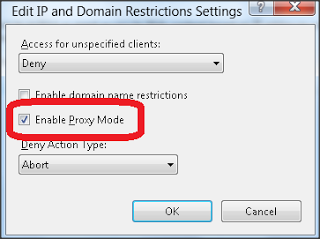
Many clients are accessing web sites through a number of proxy server ; during this case it might happen IIS might obtain same IP altogether requests though it is asked for by totally different client. To address this condition, we will configure IIS 8 to examine x-forwarded-for HTTP header. To allow this just check Enable Proxy Mode checkbox as displayed in subsequent image.
Thus in nutshell, we will claim that Dynamic IP address and domain restrictions feature of IIS 8 adds security improvements towards the web site by blocking mass requests from one client.