Most of you must be very familiar with IIS, moreover if you use Windows Server and deploy your ASP.NET application. In this tutorial, we will only give short tips about how to improve your IIS 7.5/8 performance. With good performance, IIS will serve better and faster web pages to your users.
Please Disable ASP Debugging
When you run your server in the production environment, you may not need to run ASP debugging mode. Stopping debugging mode will save you a great amount of processing power. To disable debugging, click on your server name in IIS and then right click on it to enable feature view. One the right pane, click on ‘compilation’ and then click on ‘debugging properties’. Next, set the following values as given below:
Server side debugging: false
Client side debugging: false
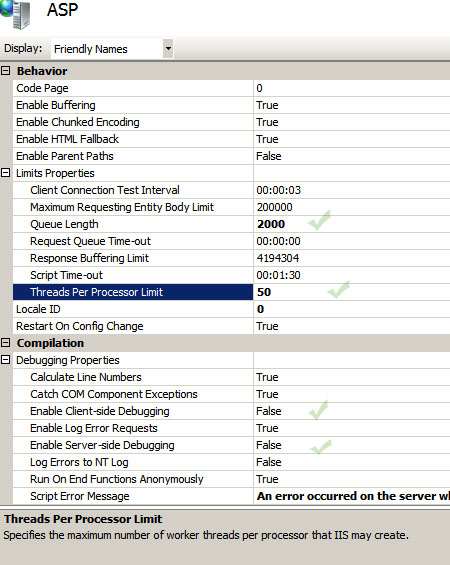
Limit ASP Threads per Processor
This limits the number of ASP requests handled by IIS simultaneously. Normally, the default value is 25. The maximum allowed number is 100. You can increase it to 50 and monitor the performance level of your IIS. To change this value click on your server and then double click on ASP under IIS in the feature view mode. Next, click on “limit properties” and set the value, as you consider suitable to match your processing needs.

Enable HTTP Compression
This is something that our clients ask to configure and it is really effective to make your site run faster. This feature helps to transfer data faster between IIS and client browsers and saves your bandwidth. You can compress HTTP in both website level and server level. To enable server level http compression, right click on sever name in IIS and then double click on compression under IIS on the right pane. You can enable both static and dynamic http compression.
Setup Logging Option
With default settings, IIS logs almost everything under the hood. You either can disable logging option or can select a number of essential events to log in your server. To set logging option, click on “Sites” in IIS server, and then select the parameters that you want to keep as a log in your server. Remember to enable the “feature view” by right clicking on the server name in IIS. In the feature view pane, click on ‘log’ and set the logging feature; to disable logging completely click on the disable option on the right pane. Remember that you can set logging option both in server level and website level.
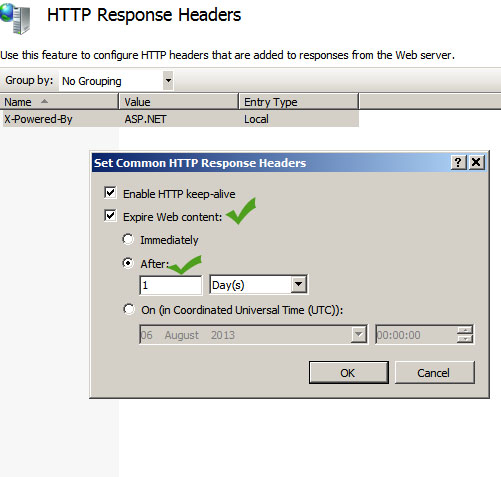
Setup HTTP Response Header
This feature helps to minimize the number of http requests send to IIS by website visitors. HTTP expires header will help the client browser to cache webpages and its elements such as images, CSS etc. To set http expires you need to click on HTTP response headers in the IIS, and then click on “set common headers”. Next select ‘expire web contents” and select the number of days or hours—this is total time your contents will be cached in the client’s browser.
Enable Output Caching
When you enable output caching, IIS will keep a copy of requested webpages. If a new user requests the very same webpage located in the cache, IIS will send the copy from its cache without reprocessing the contents. Output caching can significantly improve your server response time for dynamic contents.
Modify ASP queue length property
This value represent how often IIS will send “server too busy” message (HTTP error 503) to the users when ASP is receiving high number of requests. If the queue length time is too high, IIS will send “busy message” to users with longer delay, which make the users feel that the server may be out of service. Too low queue length will cause the server send “server busy message” quite often, consuming resources of the server. If you are unsure about this setting, you can follow Microsoft’s recommendation for one-to-one ratio, which means if you have four processors in your server with ASP thread processor value set to the default 25, you can set the queue length to 25*4=100.
You can change the queue length by going at “limit properties”—the same way you change the ASP thread processor value.
Control the connection limits
This option can give you to control the connection in three ways: controlling connection timeout, controlling maximum bandwidth per website, controlling concurrent connections.
This connection limit option will allow you to set the maximum bandwidth per second and the maximum concurrent connection per second. The maximum allowed bandwidth make a site use only a certain amount of bandwidth per second—thus improving the performance of other sites in a shared web-hosting environment.
Controlling the number of concurrent connection is another way to improve IIS performance and to improve the security of IIS as well. This option will allow only the specified number of clients to connect to the website at a given moment. So, if any malicious program tries to send numerous connection requests will be rejected by the IIS, and thus prevent your server becoming overloaded with requests during a DDoS attack.
After changing the performance settings, check the performance level of your server by gradually increasing load to a desired level. You can also consider using Google page speed tool to check whether page-loading time has been improved.
Hope above tutorial bring benefits for you. Thanks for reading.