February 21, 2020 10:50 by
 Peter
PeterToday I noticed we were getting an expanding measure of spam on one of our sform pages. I was interested to check whether the majority of the client IP locations were the same (in which case I'd simply add them to the IIS IP Restrictions list). To rapidly and effortlessly make sense of this I chose to utilize LogParser.

Other than simply questioning for the page however, I needed to add an extra condition to prohibit lines that originated from a certain internal IP address that we use for checking.
Here’s a generic version of the query I used:
LogParser.exe -q:on "SELECT * FROM x:\wwwlogs\W3SVC1\u_ex130411.log WHERE cs-uri-stem='/SomePage/' and c-ip<>'10.10.1.100' >c:\temp\PageVisitors.txt"
I needed to see the full logged information for the request, but if I didn’t, I could have very easily just pulled the IP addresses using:
LogParser.exe -q:on "SELECT c-ip FROM x:\wwwlogs\W3SVC1\u_ex130411.log WHERE cs-uri-stem='/SomePage/' and c-ip<>'10.10.1.100' >c:\temp\PageVisitors.txt"
You can see that I'm funneling the outcomes to a content record (the ">c:\temp\PageVisitors.txt" part) so I can without much of a stretch manage the outcomes. You might likewise need to observe that I'm utilizing the "-q:on" flag which runs the command in Quite Mode. In the event that you don't set this banner then LogParser will show comes about one page at once. At the point when funneling to a content record as opposed to the summon prompt window, you clearly can't hit a key for "next page" so without this banner the question will really hang forever if there is more than one page worth of results.
HostForLIFE.eu IIS 8.0 Hosting
HostForLIFE.eu is European Windows Hosting Provider which focuses on Windows Platform only. We deliver on-demand hosting solutions including Shared hosting, Reseller Hosting, Cloud Hosting, Dedicated Servers, and IT as a Service for companies of all sizes. We have customers from around the globe, spread across every continent. We serve the hosting needs of the business and professional, government and nonprofit, entertainment and personal use market segments.


February 14, 2020 10:07 by
 Peter
PeterAt this article, I’m going to tell you how search out and replace any “_” (underscore) characters in a URL .htm file name and replace it with “-” (dash). The list I used to be given had file names with up to 7 underscores in any position in IIS 7.5. Example: my_file_name.htm
While I figured this might be a straight-forward task with IIS URL Rewrite, I used to be wrong. At the end I found that I either had to form one rule for every possible underscore count or write a custom rewrite rule. I went the one rule per count route. I scan in one journal you'll only spend to nine variables (). The other a part of the rule was they'd to be only in the “/articles/” directory.
My first challenge was simply to get regular expression in place. What I seen was that the IIS 7.5 UI’s “Test Pattern” utility doesn’t accurately test. Within the test this worked:
Input: http://www.webtest.com/articles/myfilename.htm
Pattern: ^.*\/articles\/(.*)_(.*).htm$
Capture Groups: {R:1} : "my", {R:2} : "test"

However, this doesn’t match in real-world testing. #1, don’t escape “/” (forward-slash). #2 the pattern is only matched against everything after the domain and first slash. So really, only this works:
Input: http://www.test.com/articles/myfilename.htm
Pattern: ^articles/(.*)_(.*).htm$
Capture Groups: {R:1} : "my", {R:2} : "test"
When order to match against up to 8 underscores, you need 8 rules, each one looking for more underscores. So, Here is the code that I used:
Input: http://www.test.com/articles/myfilename.htm
Pattern: ^articles/(.*)_(.*)_(.*).htm$
Capture Groups: {R:1} : "my", {R:2} : "test", {R:3} : "file"
To do this with efficiency you only edit the web.config in the web root for that website. the end result concluded up being:
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<rewrite>
<rules>
<rule name="AUSx1" stopProcessing="true">
<match url="^articles/(.*)_(.*).htm$" />
<action type="Redirect" url="articles/{R:1}-{R:2}.htm" />
</rule>
<rule name="AUSx2" stopProcessing="true">
<match url="^articles/(.*)_(.*)_(.*).htm$" />
<action type="Redirect" url="articles/{R:1}-{R:2}-{R:3}.htm" />
</rule>
<rule name="AUSx3" stopProcessing="true">
<match url="^articles/(.*)_(.*)_(.*)_(.*).htm$" />
<action type="Redirect" url="articles/{R:1}-{R:2}-{R:3}-{R:4}.htm" />
</rule>
<rule name="AUSx4" stopProcessing="true">
<match url="^articles/(.*)_(.*)_(.*)_(.*)_(.*).htm$" />
<action type="Redirect" url="articles/{R:1}-{R:2}-{R:3}-{R:4}-{R:5}.htm" />
</rule>
<rule name="AUSx5" stopProcessing="true">
<match url="^articles/(.*)_(.*)_(.*)_(.*)_(.*)_(.*).htm$" />
<action type="Redirect" url="articles/{R:1}-{R:2}-{R:3}-{R:4}-{R:5}-{R:6}.htm" />
</rule>
<rule name="AUSx6" stopProcessing="true">
<match url="^articles/(.*)_(.*)_(.*)_(.*)_(.*)_(.*)_(.*).htm$" />
<action type="Redirect" url="articles/{R:1}-{R:2}-{R:3}-{R:4}-{R:5}-{R:6}-{R:7}.htm" />
</rule>
<rule name="AUSx7" stopProcessing="true">
<match url="^articles/(.*)_(.*)_(.*)_(.*)_(.*)_(.*)_(.*)_(.*).htm$" />
<action type="Redirect" url="articles/{R:1}-{R:2}-{R:3}-{R:4}-{R:5}-{R:6}-{R:7}-{R:8}.htm" />
</rule>
<rule name="AUSx8" stopProcessing="true">
<match url="^articles/(.*)_(.*)_(.*)_(.*)_(.*)_(.*)_(.*)_(.*)_(.*).htm$" />
<action type="Redirect" url="articles/{R:1}-{R:2}-{R:3}-{R:4}-{R:5}-{R:6}-{R:7}-{R:8}-{R:9}.htm" />
</rule>
</rules>
</rewrite>
</system.webServer>
</configuration>
In the end this URL:
http://www.yourdomain.com/articles/my_file_foo_bar.htm
Becomes:
http://www.yourdomain.com/articles/my-file-foo-bar.htm

February 7, 2020 11:18 by
 Peter
PeterBy default it's available only in HTTP, HTTPS and FTP protocols Windows IIS though it supports others like TCP, PIPE protocols as well.

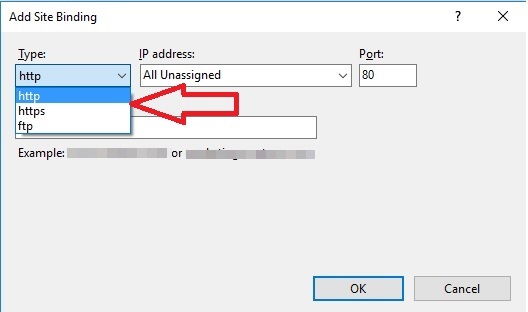
This blog demonstrates how to enable other protocols like TCP in IIS. Getting started, we know that Windows IIS by default supports only HTTP, HTTPS and FTP protocols and you will get those protocols in the binding window of IIS.
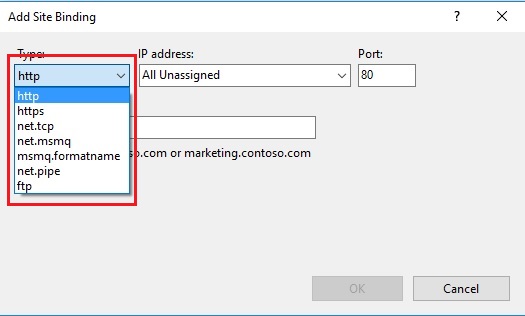
But other protocols like TCP, PIPE etc. Can be enabled by changing IIS feature, the below steps defines how to tune IIS features to enable TCP protocols.
Follow the Steps
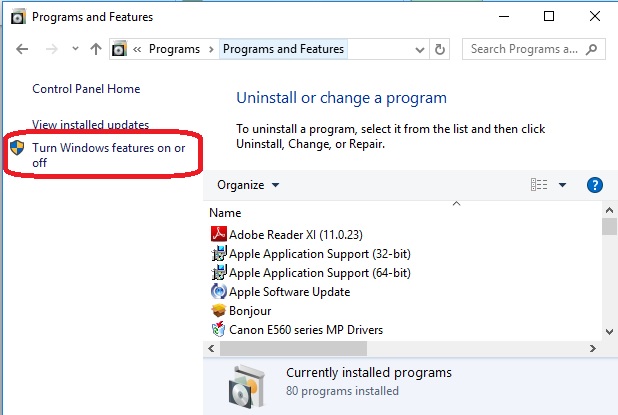
Open Control Panel=>Programs=>Click on Uninstall or Change a Program=> Click on Link ‘Turn Windows Features on or off’.
-
Windows Features window will be opened, expand .NET Framework Advance Service.
-
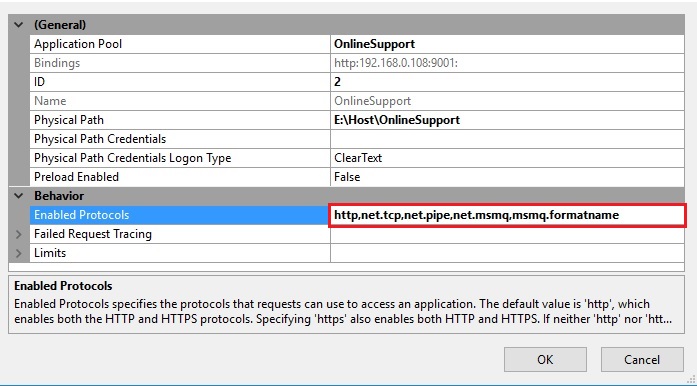
Expand WCF Services=>Select All the Features HTTPActivation, Message Queuing (MSMQ) Activation, Named Pipe Activation, TCPActivation, TCP Port Sharing .Click OK button.
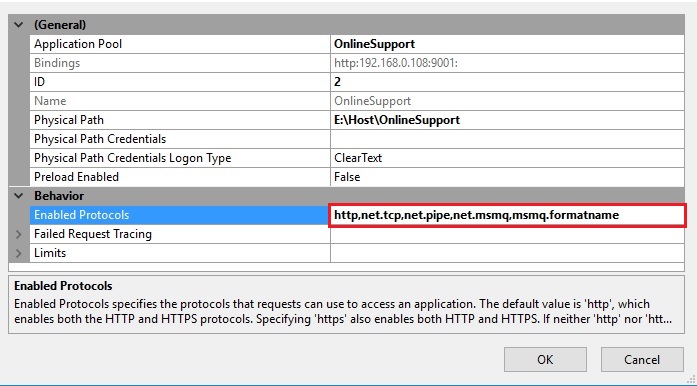
Windows will apply the changes you made and you will get message popup, close the window (Clicking on close button), restart your machine and follow the below steps. Open IIS=> in Connections panel=> expand Sites=>Select your website=>Go to Right site Action Pane=> click on Advanced Settings=> Expand the ‘Behavior’ section In the field ‘Enable Protocols’ set these below values by commas, (http,net.tcp,net.pipe,net.msmq,msmq.formatname). Click OK button.
- For activating TCP protocol set ‘net.tcp’
- For activating PIPE protocol set ‘net.pipe’
- For activating MSMQ Protocol set’ net.msmq’
Now you are done, if you follow the above steps correctly, you will get the mentioned protocols in the binding window.