
February 17, 2014 10:15 by
 Peter
PeterHostForLIFE.eu proudly launches the support of Windows Server 2012 R2 on all their newest Windows Server environment. On Windows Server 2012 R2 hosted by HostForLIFE.eu, you can try their new and improved features that deliver extremely high levels of uptime and continuous server availability start from €3.00/month.
Microsoft recently released it’s latest operating system Windows Server 2012 R2 to global customers. Microsoft Windows Server 2012 R2 is much more than just another service pack; adding new features that make it easier to build cloud applications and services in your datacenter.
Delivering on the promise of a modern datacenter, modern applications, and people-centric IT, Windows Server 2012 R2 provides a best-in-class server experience that cost-effectively cloud-optimizes your business. When you optimize your business for the cloud with Windows Server 2012 R2 hosting, you take advantage of your existing skillsets and technology investments.
You also gain all the Microsoft experience behind building and operating private and public clouds – right in the box. Windows Server 2012 R2 offers an enterprise-class, simple and cost-effective solution that’s application-focused and user centric.
Further information and the full range of features Windows Server 2012 R2 Hosting can be viewed here: http://hostforlife.eu/European-Windows-Server-2012-R2-Hosting
About Company
HostForLIFE.eu is European Windows Hosting Provider which focuses on Windows Platform only. HostForLIFE.eu deliver on-demand hosting solutions including Shared hosting, Reseller Hosting, Cloud Hosting, Dedicated Servers, and IT as a Service for companies of all sizes.

February 7, 2014 12:06 by
 Peter
Peter
Internet Information Services (IIS) 8.5 is an extensible web server created by Microsoft for use with Windows NT family. IIS 8.5 is included in Windows Server 2012 R2 and Windows 8.1. This version includes Idle worker-Process page-out, Dynamic Site Activation, Enhanced Logging, ETW logging, and Automatic Certificate Rebind.
IIS 8.5 has several improvements related to performance in large-scale scenarios, such as those used by commercial hosting providers and Microsoft's own cloud offerings. It also has several added features related to logging and troubleshooting. The new features are:
- Idle worker-Process page-out – a function to suspend idle site to reduce the memory footprint of idle sites. In IIS 8.5, the Administrator has the option of suspending an idle worker process rather than terminating it. A suspended worker process remains alive but is paged-out to disk, reducing the system resources it consumes. When a user accesses the site again, the worker process wakes up from suspension and is quickly available.
- Dynamic Site Activation – a feature that registers listening queues only to sites that have received requests.
- Enhanced Logging – Now you can customize the logging to store request headers, response headers and server variables. The customization can be used to get information such as the IP addresses of connecting clients when the network has a load balance.
- ETW logging – Event Tracing for Windows (ETW) provides application programmers the ability to start and stop event tracing sessions, instrument an application to provide trace events, and consume trace events. Trace events contain an event header and provider-defined data that describes the current state of an application or operation. You can use the events to debug an application and perform capacity and performance analysis.
- Automatic Certificate Rebind – a feature that detects when a site certificate has been renewed, and automatically rebinds the site to it

January 30, 2014 06:14 by
 Scott
Scott
HostForLIFE.eu proudly launches the support of ASP.NET 4.5.1 on all their newest Windows Server environment. HostForLIFE.eu ASP.NET 4.5.1 Hosting plan starts from just as low as €3.00/month only.
ASP.NET is Microsoft's dynamic website technology, enabling developers to create data-driven websites using the .NET platform and the latest version is 4.5.1 with lots of awesome features.
According to Microsoft officials, much of the functionality in the ASP.NET 4.5.1 release is focused on improving debugging and general diagnostics. The update also builds on top of .NET 4.5 and includes new features such as async-aware debugging, ADO.NET idle connection resiliency, ASP.NET app suspension, and allows developers to enable Edit and Continue for 64-bit.
HostForLIFE.eu is a popular online ASP.NET based hosting service provider catering to those people who face such issues. The company has managed to build a strong client base in a very short period of time. It is known for offering ultra-fast, fully-managed and secured services in the competitive market.
The new ASP.NET 4.5.1 also add support for asynchronous debugging for C#, VB, JavaScript and C++ developers. ASP.NET 4.5.1 also adds performance improvements for apps running on multicore machines. And more C++ standards support, including features like delegating constructors, raw string literals, explicit conversion operators and variadic templates.
Microsoft also is continuing to add features meant to entice more JavaScript and HTML development for those using Visual Studio to build Windows Store. Further information and the full range of features ASP.NET 4.5.1 Hosting can be viewed here http://www.hostforlife.eu/European-ASPNET-451-Hosting.

January 23, 2014 10:43 by
 Scott
Scott
HostForLIFE.eu proudly launches the support of WordPress 3.8 on all their newest Windows Server environment. HostForLIFE.eu WordPress 3.8 Hosting plan starts from just as low as €3.00/month only.
WordPress is a flexible platform which helps to create your new websites with the CMS (content management system). There are lots of benefits in using the WordPress blogging platform like quick installation, self updating, open source platform, lots of plug-ins on the database and more options for website themes and the latest version is 3.8 with lots of awesome features.
WordPress 3.8 was released in December 2013, which introduces a brand new, completely updated admin design: with a fresh, uncluttered aesthetic that embraces clarity and simplicity; new typography (Open Sans) that’s optimized for both desktop and mobile viewing; and superior contrast that makes the whole dashboard better looking and easier to navigate.
HostForLIFE.eu is a popular online WordPress hosting service provider catering to those people who face such issues. The company has managed to build a strong client base in a very short period of time. It is known for offering ultra-fast, fully-managed and secured services in the competitive market.
Another wonderful feature of WordPress 3.8 is that it uses vector-based icons in the admin dashboard. This eliminates the need for pixel-based icons. With vector-based icons, the admin dashboard loads faster and the icons look sharper. No matter what device you use – whether it’s a smartphone, tablet, or a laptop computer, the icons actually scale to fit your screen.
WordPress 3.8 is a great platform to build your web presence with. HostForLIFE.eu can help customize any web software that company wishes to utilize. Further information and the full range of features WordPress 3.8 Hosting can be viewed here http://www.hostforlife.eu.

January 15, 2014 11:35 by
 Scott
Scott
HostForLIFE.eu, a leading Windows web hosting provider with innovative technology solutions and a dedicated professional services team, today announced the supports for Umbraco 7 Hosting plan due to high demand of Umbraco 7 CMS users in Europe. Umbraco 7 features the stable engine of Umbraco 6 powering hundreds of thousands of websites, but now enriched with a completely new, remarkably fast and simple user interface.

Umbraco is fast becoming the leading .NET based, license-free (open-source) content management system. It is an enterprise level CMS with a fantastic user-interface and an incredibly flexible framework which is both scalable and easy to use. Umbraco is used on more than 85,000 websites, including sites for large companies such as Microsoft and Toyota.
HostForLIFE.eu is a popular online Umbraco 7 hosting service provider catering to those people who face such issues. The company has managed to build a strong client base in a very short period of time. It is known for offering ultra-fast, fully-managed and secured services in the competitive market.
Umbraco has given a lot of thought to the user experience of their CMS. The interface uses a navigational flow and editing tools that anybody using Windows Explorer and Microsoft Word will immediately recognise. Your site structure sits in a tree view - just like Windows Explorer. Anybody with experience using Microsoft Word, can use Umbraco's simple rich text editing (RTE) interface.
"Umbraco 7 is easy to install within few clicks, special thanks to HostForLIFE.eu special designed user friendly web hosting control panel systems." - Ivan Carlos, one of the many HostForLIFE.eu satisfying clients.
Further information and the full range of features Umbraco 7 Hosting can be viewed here http://hostforlife.eu/European-Umbraco-7-Hosting.
HostForLIFE.eu, a leading Windows web hosting provider with innovative technology solutions and a dedicated professional services team proudly announces Enterprise Email Hosting for all costumer. HostForLIFE.eu aim to help you grow your bottom line whether it is driving direct sales from emails, driving website traffic or delivering outstanding service.
Enterprise Email is a great tool for communicating to existing customers, or individuals who know your organization well enough and have interest in opting-in to receive your e-mail. Your promotions, sales and offers get their attention, meet a need, and encourage them to do more business with you. What e-mail marketing typically doesn’t do very effectively is attract the attention of new customers.
Robert Junior and Sophia Levine from HostForLIFE.eu say:
"Once a business has secured a domain name, we setup an email hosting account for them and they can choose any email account they wish. Most popular email accounts for small business are sales, info and accounts, although it can be virtually anything once you own your own domain name." Robert says.
"I would expect that once more small business owners had the flexibility to mange their own email hosting, they would save money on their monthly internet costs because there are always cheaper deals being promoted. Of course email hosting does not replace your internet service, but it enables you to switch to a cheaper plan and not loose contact with your customers." Sophia says.
"Our clients have found that they are able to save money on their internet services because once they no longer rely to manage their email, they can shop around for a better deal, save some money and take their Email Hosting with them. Having your own domain name and email hosting also improves your business image far more that an ISP account or hotmail email address." Robert says.
"What many small business owners often struggle with is continuing to pay high internet service costs to keep their allocated ISP email address if they use their ISP email for their business. What people do not realise is that if they were to purchase their own .com or etc domain name they have a unique email address like '[email protected]'. It means they can move to a cheaper ISP if they find a better deal and not risk losing contact with their business contacts." Sophia Says.
HostForLIFE.eu provides a full suite of self-service marketing solutions with the following features: Total Bulk Email up to 10.000 emails/month with total maibox is 5, users receive 2 GB mailbox quota, a platform fully support Blackberry, SPF/DKIM/TXT, WebMail Access, and POP/SMTP/IMAP.
Are you sending direct mails to your customers just once a month or every three days? Simply choose the plan that suits you the most. All price plans are based on actual use of the system - from 10,000 e-mails sent out in a month starting at €8.00!
Further information and the full range of features Enterprise Email Hosting can be viewed here http://www.hostforlife.eu.
By default, SmarterMail installs a basic web server that allows administrators to start using the application immediately after installation. However, SmarterTools recommends moving to a more robust and secure Web server, such as Microsoft IIS.
Applies to SmarterMail 8 - 11.x
This article covers the following:
- Disabling the SmarterMail Web server
- Adding IIS ISAPI components
- Adding a new application pool for SmarterMail
- Adding SmarterMail to IIS 8
- Verifying IIS Settings
- Updating DNS
- Testing the site
Disabling the SmarterMail Web Server
These steps will stop and disable the default web server that is included with SmarterMail. This will also have the side-effect of disabling any shortcut for SmarterMail that may be placed on your desktop until you update it with the new URL for the SmarterMail site created in IIS.
- Click on Start -> Programs -> SmarterTools -> SmarterMail -> Configure SmarterMail Web Server
- Click on the Stop button
- Change the Startup Mode to Disabled
- Click on the Apply button
- Click the Close button
- Add IIS ISAPI Components
Follow these sets to add the necessary IIS components
- Open up IIS
- When prompted Launch Internet Information Services (IIS) Manager
- Click on Products tab
- Click on Servers
- Install required components of: IIS: ASP.NET, .NET Extensibility, ASP, CGI, ISAPI Extensions, ISAPI Filters
- Install any other options components
- Click Install
Add an Application Pool
Follow these steps to add an application pool specifically for SmarterMail:
- Open Internet Information Services (IIS) Manager
- Right click on Application Pools from the tree view and choose Add Application Pool
- Name the new application pool SmarterMail, or something similarly easy to identify
- Set the .Net Framework Version to v4.0.x
- Set the Application Pools Managed Pipeline to 'Integrated'
- Make sure "Start application pool immediately" is checked
- Click OK
Add SmarterMail to IIS 8
Follow these steps to add SmarterMail to IIS 8:
- Open Internet Information Services (IIS) Manager
- Click on your ServerName, and on the right side, under IIS, double-click ISAPI and CGI Restrictions
- Verify that ASP.NET v4.0 is allowed (If not, right click on ASP.NET v4.0.x and select Allowed)
- On the left side of the page, right click on Sites in the tree view and choose Add Website
- Name the site SmarterMail
- If you created an Application Pool name other than SmarterMail, click Select and choose the correct Application Pool
- For the physical path, browse to the SmarterMail -> MRS folder. The default location is C:\Program Files (x86)\SmarterTools\SmarterMail\MRS
- For Binding, choose an IP address to use for Webmail. If this IP address is shared with another Web site, you will need to use a different port or Host Headers. For more information about using Host headers, refer to the IIS documentation
- Make sure "Start Web site immediately" is checked
- Click OK
Verify IIS Settings
Follow these steps to verify the IIS settings. Please read each item carefully.
- In IIS Manager, click on your ServerName
- Under IIS, double click ISAPI and CGI Restrictions
- Verify that ASP .NET v4.0 is allowed. If it is not, right-click on ASP .NET v4.0 and select Allowed
- In the tree view, click Sites
- Expand (or double click) the SmarterMail site
- Click on the App_Themes folder
- Under IIS, double click HTTP Response Headers
- Under the Action menus, click Set Common Headers
- Enable the Expire Web content setting
- Click OK
- Click on Application Pools in the tree view
- Right click on the SmarterMail application pool and select Advanced Settings
- Under the Process Model heading, ensure the the Identity is set to the NetworkService account
- From the Start menu, open Administrative Tools and select Services, then verify that the World Wide Publishing Service is running
KeePass is an open source password manager. The passwords are stored in a database with the .kdbx extension. The database can be on your local file system or on a web server. If you put the database on an IIS webserver, you can access it from KeePass, but if you try to save, you get a 404 error.This is because the StaticFile HTTP handler in IIS only supports the GET method and KeePass requires PUT, MOVE and DELETE, in addition to GET.
To add support for this, a custom HTTP handler has to be added to the webserver. The HTTP handler is a C# library project with a class that implements IHttpHandler. A reference to System.Web needs to be added.
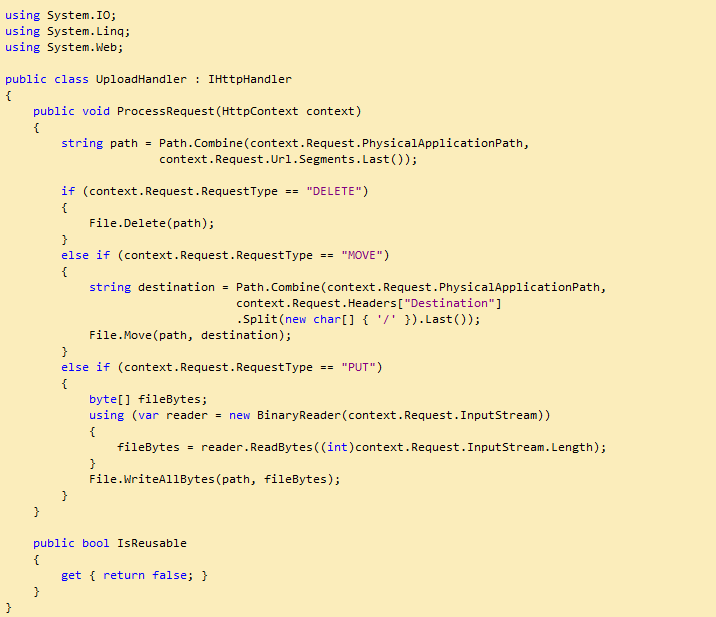
To add the handler, put the following in web.config:
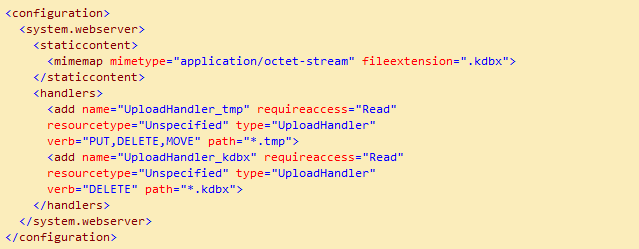
Put the library DLL in a folder named "bin" on the web site.
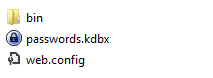
Now, you should be able to save your KeePass database!
HostForLIFE.eu offers a variety of cheap and affordable European Windows ASP.NET Shared Hosting Plans to fit any need. No matter whether you’re starting a Blog with WordPress, installing a CMS solution with Drupal, opening a Forum with PHPBB, starting an Online Store with nopCommerce, or any number ventures beyond those mentioned above, our Windows ASP.NET Web Hosting plans are exactly what you’ve been looking for. HostForLIFE.eu is Microsoft No #1 Recommended ASP.NET Host Provider.
Entity Framework 6 (EF6) is an object-relational mapper that enables .NET developers to work with relational data using domain-specific objects. It eliminates the need for most of the data-access code that developers usually need to write.
Entity Framework is now available and there are top features to consider in this minor release:
Features that come for free. These are capabilities that are part of the core. You don’t even have to know they’re there to benefit from them, much less learn any new coding.
Level-setting features. A major enhancement is that Code First now supports mapping to Stored Procedures, something that has been supported by models created in the designer.
Another change is more interesting. With EF6, the EF APIs have been extracted from the .NET Framework; they’re now completely encapsulated in the NuGet package.
EF Designer in this category. It has been moved out of Visual Studio as of the 2013 edition, and instead provided as an extension to Visual Studio.
Ninja features. Support for asynchronous queries and saves, the return of custom Code First conventions, more extensibility using the new DbConfiguration type, support for mocking in unit tests, configurable retries on spotty connections, and even more.
For complete information about this new product, please visit our site at http://www.hostforlife.eu
Do you ever encountered an error if you deploying WebSocket server application which targeted .NET 4.5 to Windows Server 2012 plus IIS 8? Yes, it was an exception shown in browser whenever tried to open a web page. The exception said:
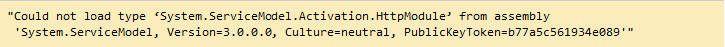
This problem is: the default configuration in applicationHost.config (in C:\Windows\System32\inetsrv\config) declared two conflicted modules and two conflicted handlers:
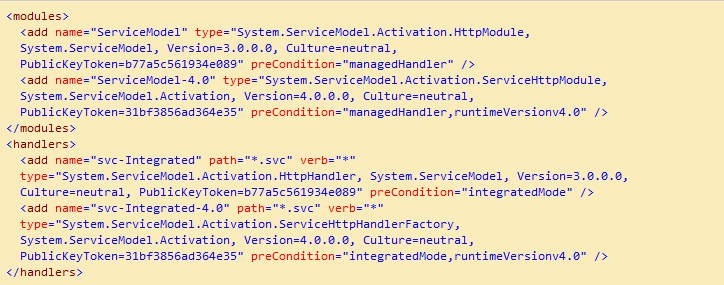
As we know, applicationHost.config contains the root settings for all web sites and web applications on the server. Therefore, any web application would have all the four conflicted modules and handlers loaded by default. “ServiceModel” and “svc-Integrated” were for .NET Activation 3.x while “ServiceModel-4.0” and “svc-Integrated-4.0” were for .NET Activation 4.x. Unfortunately, the 3.x items were declared before the 4.x items. That was why the exception occurred for a .NET 4.x web application!
Then how did such a situation happen? On Windows Server 2008, it could happen when you install .NET 3.x framework or IIS 7.5 with Activation features after .NET framework 4.x is installed. However, on Windows Server 2012, it always happens when you install .NET framework 3.x with Activation features.

Microsoft officially announced the solution (http://support.microsoft.com/kb/2015129) for Windows Server 2008 plus IIS 7.5: manually running “aspnet_regiis.exe /iru” for .NET framework 4.x (in C:\Windows\Microsoft.NET\Framework\v4.0.30319 or C:\Windows\Microsoft.NET\Framework64\v4.0.30319). However, aspnet_regiis.exe is not allowed to run for IIS 8.
The final solution was to delete the 3.x module and handler from IIS manager. You could delete them at the application or site level if you want to keep them in applicationHost.config. But if you wanted to delete them from applicationHost.config. So you should did the following steps:
1. In IIS manager, click the machine name node.
2. In “Features View”, double-click “Modules”.
3. Find “ServiceModel” and remove it.
4. Go back to the machine name node’s “Features View”, double-click “Handler Mappings”.
5. Find “svc-Integrated” and remove it.
Now everything works well.