Now, I want to do the same thing, but this time, using PowerShell. We can easily achieve this with the help of PowerShell and typing a few simple commands.

Before we begin with DHCP installation process, first we need to make sure that it’s not installed in our Server 2016. We can verify this in two ways., which are given below.
- Using Server Manager.
- Using PowerShell.
As you can see below, I opened my Server Manager to check (Left side , under Dashboard), if DHCP is already installed, as we can see in the screenshot given below, DHCP Server roles are not installed yet.
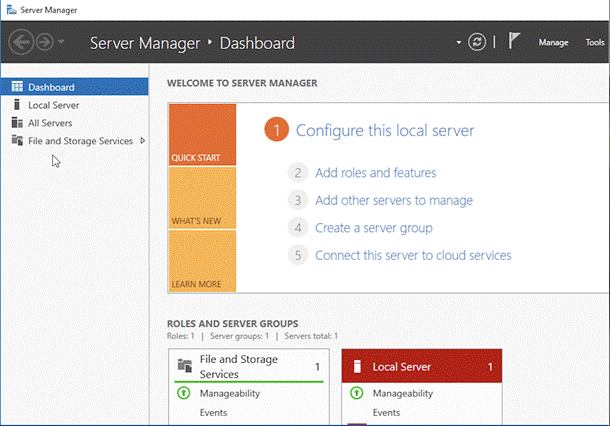
Server Manager
Let’s verify this, using PowerShell. All you need to do is, just open your PowerShell and type the command given below.
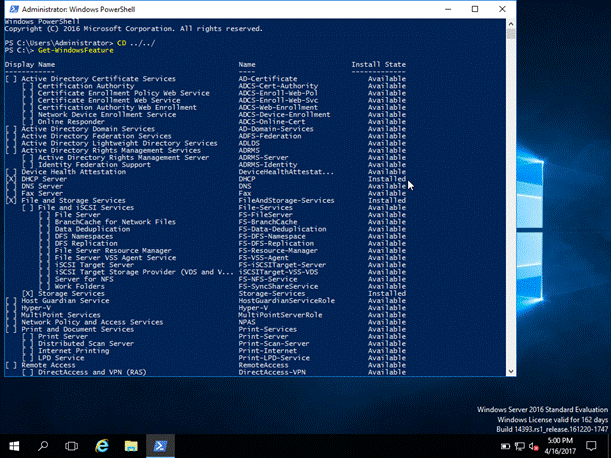
Get-WindowsFeature
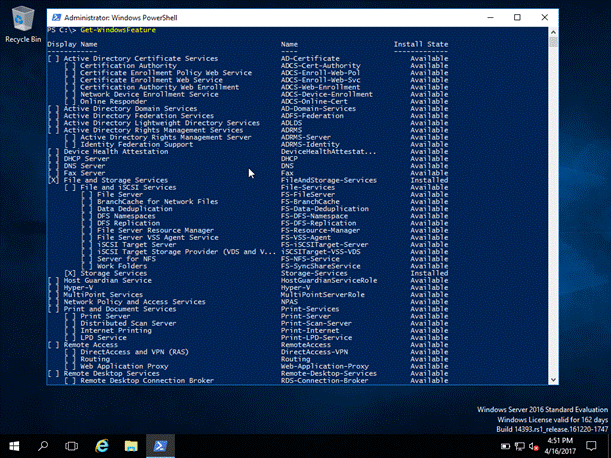
You can notice in the screenshot given above, install Sate for DHCP says “Available”, which means that it’s available for the installation and it’s not installed yet. Thus, we can continue with our installation process..
To install this DHCP server role using PowerShell, we need to use the command given below.
Install-WindowsFeature -Name ‘DHCP’
After installing this DHCP Server role, type the commands given below to install DHCP Management Tools.
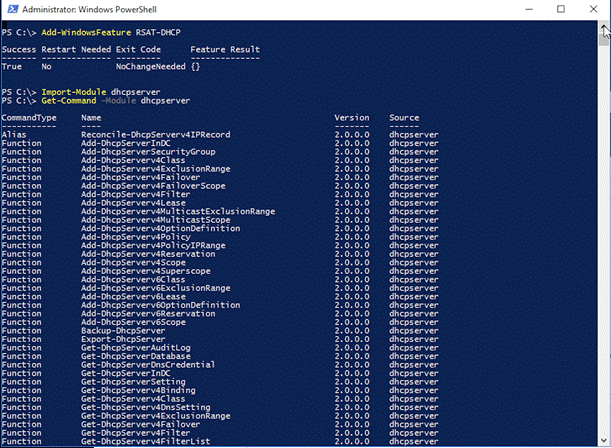
We have successfully installed DHCP Server role and all the required tools to manage it. We can verify this in two ways. We can go back to Server Manager to see, if there is a DHCP Server role, the other way is suing PowerShell…Let’s first verify this, using Server Manager.
Go to —> Server Manager and check for DHCP under Roles and Server Groups (See the screenshot given below.)
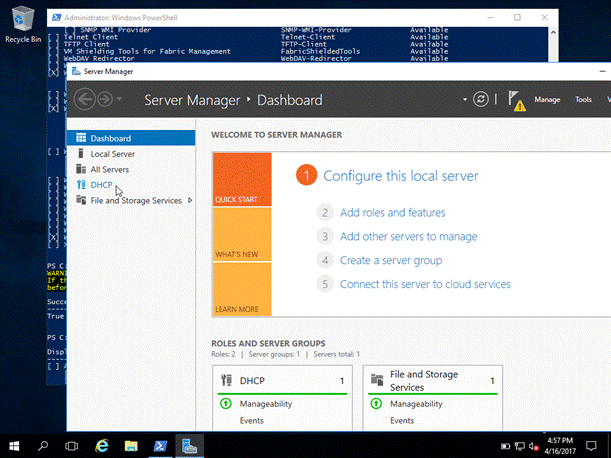
We can also verify this using PowerShell, using the command given below.
Get-WindowsFeature.
HostForLIFE.eu IIS 8.0 Hosting
HostForLIFE.eu is European Windows Hosting Provider which focuses on Windows Platform only. We deliver on-demand hosting solutions including Shared hosting, Reseller Hosting, Cloud Hosting, Dedicated Servers, and IT as a Service for companies of all sizes. We have customers from around the globe, spread across every continent. We serve the hosting needs of the business and professional, government and nonprofit, entertainment and personal use market segments.
